Unlocking the world of ExtraTorrents becomes seamless with the power of proxies, providing a gateway to a vast array of downloadable content.
Dive into the realm of limitless downloads as ExtraTorrents proxies break down barriers, ensuring a seamless and private torrenting experience for enthusiasts worldwide.
Unlocking ExtraTorrents with Alternate Routes – Stream Safely!
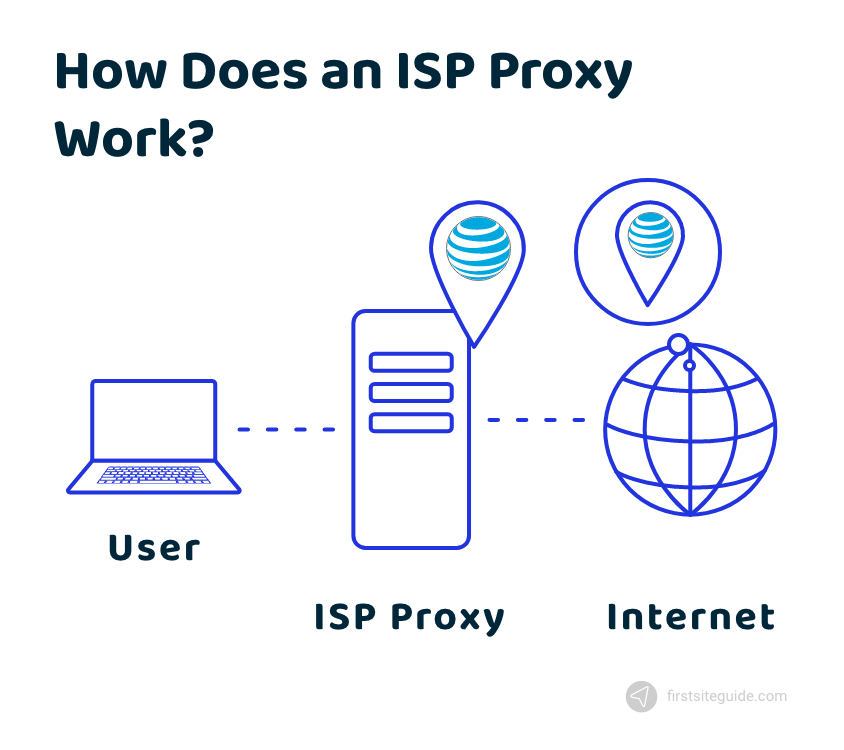
ExtraTorrents proxies play a pivotal role as intermediary servers, providing users with the capability to circumvent restrictions imposed by Internet Service Providers (ISPs) or governmental bodies.
Operating as intermediaries, these proxies replicate the content of the authentic ExtraTorrents site, granting users access to torrent files without establishing a direct connection to the primary server.
Essentially, the proxies act as virtual conduits, allowing users to navigate around imposed barriers and securely access the desired content, ensuring a more unrestricted and confidential torrenting experience.
The Importance of Proxies – Explore significance!
1. Circumventing ISP Blocks:
In specific regions, Internet Service Providers (ISPs) may restrict access to ExtraTorrents due to apprehensions related to copyright infringement. Proxies emerge as a practical workaround, serving as intermediaries that enable users to bypass these imposed restrictions.
By utilizing proxies, users can effectively navigate through the ISP barriers, ensuring access to ExtraTorrents even in regions where such restrictions are in place. This circumvention allows users to engage with the platform, access torrent files, and enjoy content without hindrance, providing a solution to the challenges posed by ISP-imposed access limitations.
2. Ensuring Anonymity:

Proxies play a pivotal role in preserving user anonymity by acting as a protective shield between the user and the ExtraTorrents server. This additional layer of privacy is particularly crucial for individuals aiming to safeguard their online identity.
By routing internet traffic through a proxy, users obscure their IP addresses and conceal their digital footprint, making it challenging for external entities, including ExtraTorrents servers, to trace their online activities. This heightened level of privacy empowers users to engage with ExtraTorrents securely, ensuring that their personal information remains confidential and their online identity is shielded from potential threats or surveillance.
3. Proxy Reliability:
The effectiveness and reliability of proxies may vary, posing a challenge for users who rely on these intermediaries to access ExtraTorrents. Inconsistent proxy performance can lead to disruptions and hinder the seamless torrenting experience.
4. Legal Concerns:
The use of proxies to access ExtraTorrents may raise legal concerns in certain regions. Users need to be aware of the legal implications and potential consequences related to circumventing restrictions, especially when it comes to copyright laws.
5. Security Risks:
While proxies aim to enhance user security, using unreliable or unauthenticated proxies can expose users to security risks. Malicious proxies may compromise user data, leading to privacy breaches and potential cyber threats.
6. ISP Vigilance:
ISPs may actively monitor and block proxy access to ExtraTorrents, especially in regions where torrenting is subject to legal restrictions. Users may encounter challenges as ISPs employ measures to detect and restrict proxy usage.
5. Proxy Authenticity Verification:
Verifying the authenticity of proxies requires user diligence, and the process can be time-consuming. Users may face challenges in ensuring that the selected proxies are legitimate, leading to potential security issues if not adequately verified.
8. Limited Content Access:
Some proxies may not fully mirror the content available on the original ExtraTorrents site. Users might face challenges accessing specific content or features, limiting the comprehensiveness of their torrenting experience.
9. Constant Updates and Changes:
ExtraTorrents and proxy services undergo continuous updates and changes. Users may find it challenging to stay informed about these updates, potentially causing disruptions or making previously reliable proxies obsolete.
10. VPN Compatibility:
While VPNs offer an additional layer of security, users may encounter compatibility challenges when using both proxies and VPNs simultaneously. Ensuring proper configuration and compatibility can be a technical challenge for some users.
Tips for a Secure Experience – Torrent Safely!
1. Verify Proxy Authenticity:
It is imperative for users to take a proactive role in safeguarding their online security by independently verifying the authenticity and safety of any proxy intended for use, particularly when accessing ExtraTorrents or other online content.
This precautionary measure is crucial due to the significant risks associated with unreliable proxies that have the potential to compromise user security.
Users should prioritize the authentication of proxies, confirming their legitimacy and affiliation with ExtraTorrents while steering clear of potentially malicious entities. Obtaining proxies from reputable sources, supported by positive user reviews and recommendations, contributes to a more secure browsing experience.
Additionally, users should scrutinize proxies for security features such as encryption and data protection, favoring those that implement robust measures to safeguard user information. Regular updates from proxy providers are essential to ensure ongoing security and optimal performance.
Furthermore, users are advised to avoid free or unknown proxies, opting instead for proxies from reputable providers even if they involve a reasonable cost. Considering the use of a Virtual Private Network (VPN) in conjunction with a proxy can provide an added layer of security by encrypting user data.
A trial or testing period before regular use allows users to assess the proxy’s performance and security features, identifying and addressing potential issues proactively.
2. Use VPN Services:

To enhance security while accessing ExtraTorrents or engaging in any online activities, users should consider integrating a Virtual Private Network (VPN). VPNs offer an additional layer of protection by concealing user IP addresses and encrypting data.
This encryption ensures that sensitive information remains secure during transmission, providing a fortified and anonymous browsing experience.
By routing internet traffic through a VPN, users can safeguard their online identity, thwart potential cyber threats, and enjoy a heightened level of privacy, making VPNs a valuable tool for those seeking a secure digital environment.
3. Stay Informed:
It is advisable for users to consistently monitor updates regarding the status of ExtraTorrents and the efficacy of proxies. Staying informed about any changes ensures a seamless and secure torrenting experience.
By regularly checking for updates, users can stay ahead of potential disruptions, modifications, or improvements to ExtraTorrents and the associated proxy services.
This proactive approach allows users to adapt their strategies accordingly, ensuring continuous access to the platform while maintaining a high level of security. Awareness of any alterations or developments in the torrenting landscape contributes to a more informed and secure user experience.
Conclusion:
In the end
Effortlessly unlock ExtraTorrents with proxies for a world of downloads. These digital guardians navigate ISP barriers, ensuring secure torrenting. Break down barriers with ExtraTorrents proxies, ensuring a seamless and private torrenting experience.
FAQs
1. Why should I use ExtraTorrents proxies?
Proxies provide a secure gateway, allowing you to access ExtraTorrents and download content despite regional restrictions.
2. How do proxies ensure user anonymity on ExtraTorrents?
Proxies act as a shield, concealing your IP address and preserving online identity while navigating ExtraTorrents.
3. What’s the significance of verifying proxy authenticity?
Verifying proxies ensures secure browsing, protecting against potential risks and maintaining user security on ExtraTorrents.
Read Also:











+ There are no comments
Add yours